What this module adds: Sentinel incident ingestion, Content Management System (CMS) for detection rules, email notifications, log search, and Azure Lighthouse cross-tenant management.
Prerequisites
Before starting, ensure you have the following:Global Administrator
Azure Role for Microsoft Tenant: Global Admin or Security Admin
Workspace Owner
ContraForce Workspace Role: Owner or Admin
Subscription Owner
Microsoft Subscription Permission: Owner
Additional Requirements
| Requirement | Details |
|---|---|
| Microsoft Sentinel | Active Sentinel workspace in your Azure subscription |
| Log Analytics Workspace | The workspace linked to your Sentinel deployment |
| Resource Group Access | Ability to create resources in the subscription |
| No Conflicting Policies | Azure Policy must allow Lighthouse delegations |
What Gets Deployed
The Sentinel module deploys several Azure resources to enable integration:| Component | Purpose |
|---|---|
| Azure Lighthouse | Cross-tenant delegation for multi-tenant management |
| Apollo Resource Group | Infrastructure for incident streaming |
| Logic App | Streams Sentinel incidents to ContraForce in real-time |
| Automation Rule | Triggers the Logic App when incidents are created/updated |
| Role Assignments | Grants ContraForce service principals access to Sentinel |
Azure Resources Reference
Complete list of all deployed resources with details
Step 1: Navigate to Sentinel Configuration
Open Your Workspace
From the ContraForce portal, navigate to Workspaces and select the workspace you want to configure
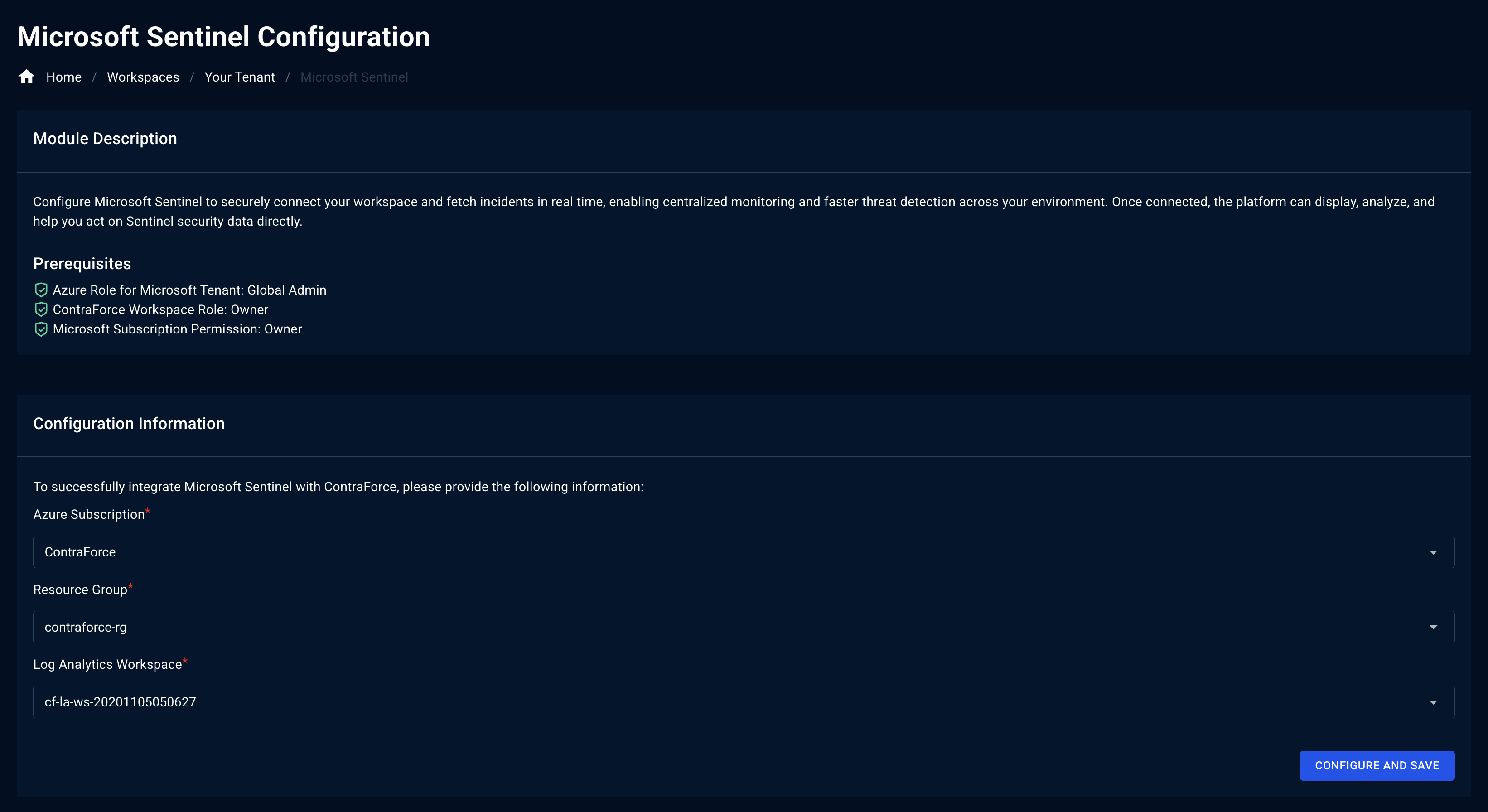
Step 2: Verify Prerequisites
The configuration screen displays prerequisite checks. Ensure all items show a green checkmark:| Prerequisite | Required Value |
|---|---|
| Azure Role for Microsoft Tenant | Global Admin |
| ContraForce Workspace Role | Owner |
| Microsoft Subscription Permission | Owner |
If any prerequisite shows a red X, you’ll need to obtain the required permissions before proceeding. The deployment will fail without proper access.
Step 3: Provide Configuration Information
Enter your Azure environment details:Select Azure Subscription
From the Azure Subscription dropdown, select the subscription containing your Sentinel workspace
Select Resource Group
From the Resource Group dropdown, select the resource group containing your Sentinel/Log Analytics workspace
Configuration Fields
| Field | Description | Example |
|---|---|---|
| Azure Subscription | The subscription containing Sentinel | ”Production-Security” |
| Resource Group | Resource group with your Sentinel workspace | ”rg-sentinel-prod” |
| Log Analytics Workspace | Your Sentinel/Log Analytics workspace | ”la-sentinel-workspace” |
Step 4: Configure and Save
Authenticate if Prompted
You may be prompted to sign in with your Azure credentials. Use an account with Subscription Owner permissions.
Step 5: Deploy Azure Lighthouse
After the initial configuration, you’ll need to deploy Azure Lighthouse for cross-tenant management.Navigate to Lighthouse Deployment
The wizard will automatically proceed to the Lighthouse deployment step, or you can find it in the Modules tab
Authorize in Azure
A new window will open to the Azure portal. Review the delegation details and click Create
What Lighthouse Enables
| Capability | Description |
|---|---|
| Cross-tenant visibility | View and manage Sentinel from the ContraForce portal |
| Incident access | Read and update incidents across tenants |
| Query execution | Run Log Analytics queries for threat hunting |
| Rule deployment | Deploy detection rules via CMS |
Step 6: Deploy Apollo Infrastructure
Apollo is the incident streaming infrastructure that enables real-time incident notifications.Apollo Resources Created
| Resource | Type | Purpose |
|---|---|---|
| cf-apollo-[workspace] | Resource Group | Container for streaming resources |
| cf-incident-stream | Logic App | Processes and forwards incidents |
| cf-sentinel-connection | API Connection | Authenticates to Sentinel |
| cf-incident-trigger | Automation Rule | Triggers on incident changes |
Apollo resources are created in the customer’s Azure subscription. Standard Azure charges may apply for Logic App executions.
Step 7: Consent Sentinel Enterprise Applications
The Sentinel module requires additional enterprise application consent.Navigate to Enterprise Apps Section
In the onboarding wizard, proceed to the enterprise application consent step
Sentinel Application Permissions
| Application | Permissions | Purpose |
|---|---|---|
| ContraForce Sentinel Hunting | Log Analytics Reader | Execute KQL queries for threat hunting |
Step 8: Verify Module Status
Confirm the Sentinel module is fully configured:Module Status Checklist
- Microsoft Sentinel module shows Active
- Azure Lighthouse shows Active
- Apollo shows Active
- ContraForce Sentinel Hunting shows Consented
Test Incident Sync
Post-Configuration Steps
Configure Notifications
With the Sentinel module active, you can now configure email notifications:Notifications Configuration
Complete guide to notification setup
Deploy Detection Rules
Use the Content Management System to deploy detection rules to your Sentinel workspace:CMS Onboarding
Deploy detection rules to your Sentinel workspace
Troubleshooting
Common Issues
| Issue | Cause | Solution |
|---|---|---|
| Subscription not visible | Insufficient permissions | Sign in with Subscription Owner account |
| Deployment fails | Azure Policy restrictions | Check for policies blocking Lighthouse or resource creation |
| Lighthouse deployment fails | Existing delegation | Remove existing Lighthouse delegation and retry |
| No incidents appearing | No incidents in Sentinel | Verify incidents exist in the Sentinel portal |
| Apollo Logic App disabled | Deployment issue | Manually enable the Logic App in Azure portal |
| Consent popup blocked | Browser settings | Allow popups from portal.contraforce.com |
Verifying Azure Resources
To verify resources deployed correctly:Open Azure Portal
Navigate to portal.azure.com
Lighthouse Troubleshooting
If Lighthouse delegation fails:- Check Azure Policy — Some organizations restrict Lighthouse delegations
- Remove existing delegations — Conflicting delegations can cause failures
- Verify permissions — Subscription Owner is required
- Check tenant settings — Ensure cross-tenant access isn’t blocked
How to remove existing Lighthouse delegation
How to remove existing Lighthouse delegation
- Go to Azure Portal → Service providers
- Find any existing ContraForce delegations
- Click on the delegation and select Delete
- Wait for deletion to complete
- Retry the deployment in ContraForce
How to enable Logic App manually
How to enable Logic App manually
- Go to Azure Portal → Resource Groups
- Open the cf-apollo-[workspace] resource group
- Click on the Logic App resource
- Click Enable if the Logic App is disabled
- Verify the Logic App shows “Enabled” status
Module Capabilities Unlocked
With the Sentinel module configured, you now have access to:Sentinel Incidents
Real-time incident ingestion from Microsoft Sentinel
Email Notifications
Instant alerts when new incidents are created
Content Management System
Deploy and manage detection rules at scale
Log Search
Query Log Analytics for threat hunting
Cross-Tenant Management
Manage multiple Sentinel workspaces from one portal
Advanced Threat Hunting
Execute KQL queries across customer environments
Next Steps
Configure Notifications
Set up email alerts for incidents
Deploy Detection Rules
Use CMS to deploy Sentinel rules
Add Users
Grant team access to the workspace
Incident Management
Start triaging Sentinel incidents
Related Guides
XDR Module
Defender XDR integration
Azure Resources
Complete resource reference
CMS Overview
Detection rule management
Need help with Sentinel module deployment? Contact us at support@contraforce.com.

