CMS is available for workspaces with the Microsoft Sentinel module deployed. Within CMS, a library of expert-developed detection rules are available under the Sentinel Marketplace tab. Your existing rules can be viewed under the Analytic Rules tab.
Why CMS?
Expert-Authored Rules
Detection content written by security engineers covering MITRE ATT&CK
One-Click Deployment
Enable rules with a toggle—no complex configuration, no multi-step installations
Multi-Tenant Scale
Deploy the same rules across one customer or hundreds
Automatic Updates
Keep detection rules current as threats evolve, with optional auto-update
The Problem CMS Solves
Security teams face what we call “the content storm”—the overwhelming challenge of creating, deploying, and maintaining detection rules at scale.Traditional Challenges
Expertise Requirements
Expertise Requirements
Writing effective detection rules requires deep knowledge of KQL (Kusto Query Language), understanding of attack techniques, and familiarity with Microsoft Sentinel’s rule configuration options. This expertise is expensive and hard to find.
Time-Intensive Maintenance
Time-Intensive Maintenance
Threats evolve constantly. Detection rules that worked yesterday may miss today’s attack variants. Keeping rules current across multiple customer environments is a never-ending task.
Scaling Difficulties
Scaling Difficulties
What works for one Sentinel workspace becomes exponentially harder when managing dozens or hundreds of customer environments. Microsoft’s native interface requires navigating through each tenant individually.
Configuration Complexity
Configuration Complexity
Deploying a single rule in Sentinel’s native interface involves multiple steps—finding the template, configuring parameters, setting schedules, mapping entities. Multiply this across hundreds of rules and many tenants, and the burden becomes unsustainable.
How CMS Works
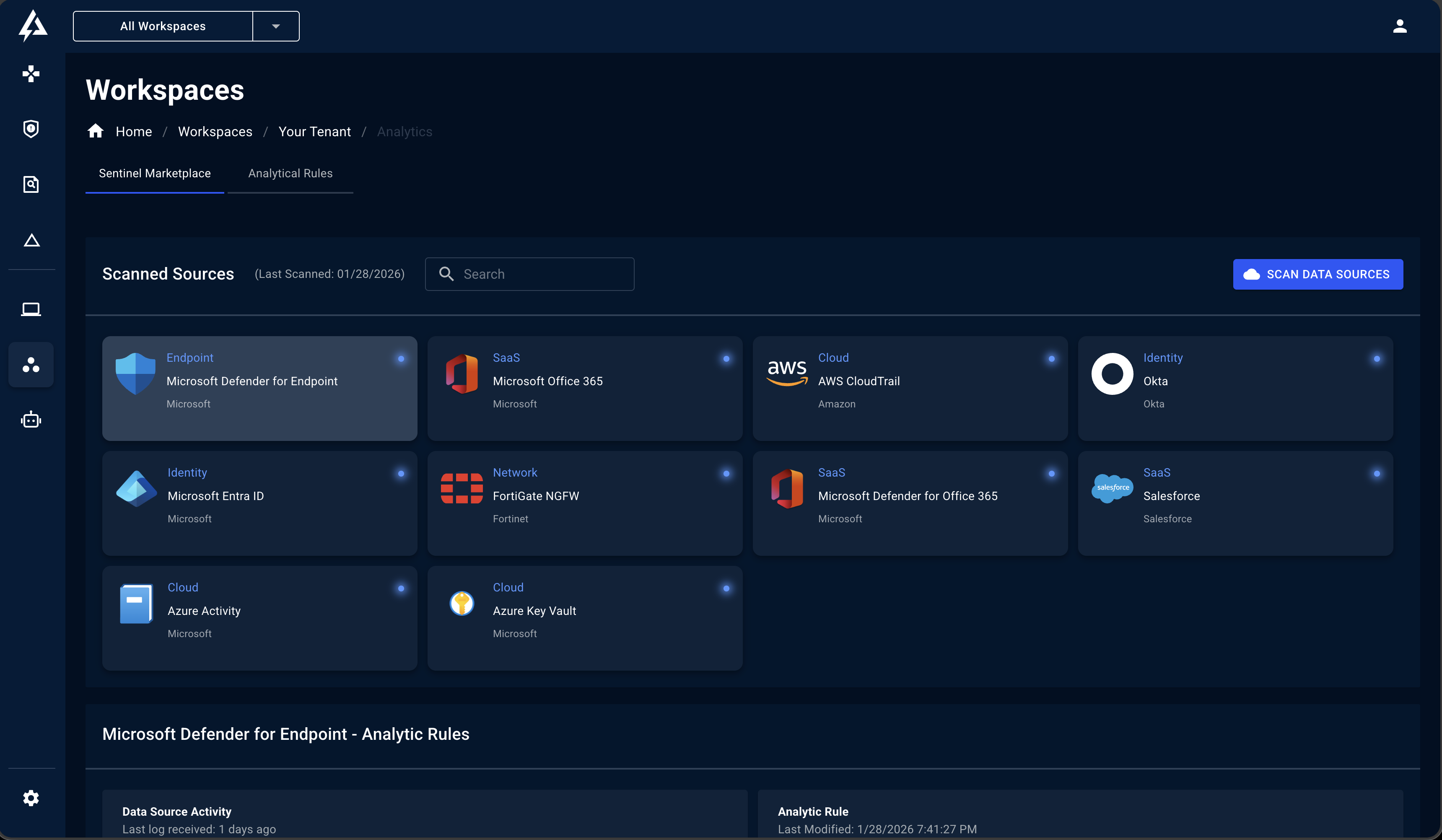
Detection Rule Library
CMS provides access to a continuously updated library of detection rules organized by data source. Each rule includes:| Attribute | Description |
|---|---|
| Display Name | Clear, descriptive name for the detection |
| Description | What the rule detects and why it matters |
| Severity | Risk level (Low, Medium, High) to prioritize response |
| MITRE ATT&CK Mapping | Tactics and techniques the detection covers |
| Query | The underlying KQL logic (visible for transparency) |
| Version | CalVer format (e.g., 2024.01.15) for tracking updates |
| Query Frequency | How often the rule runs |
| Query Period | The time window the rule analyzes |
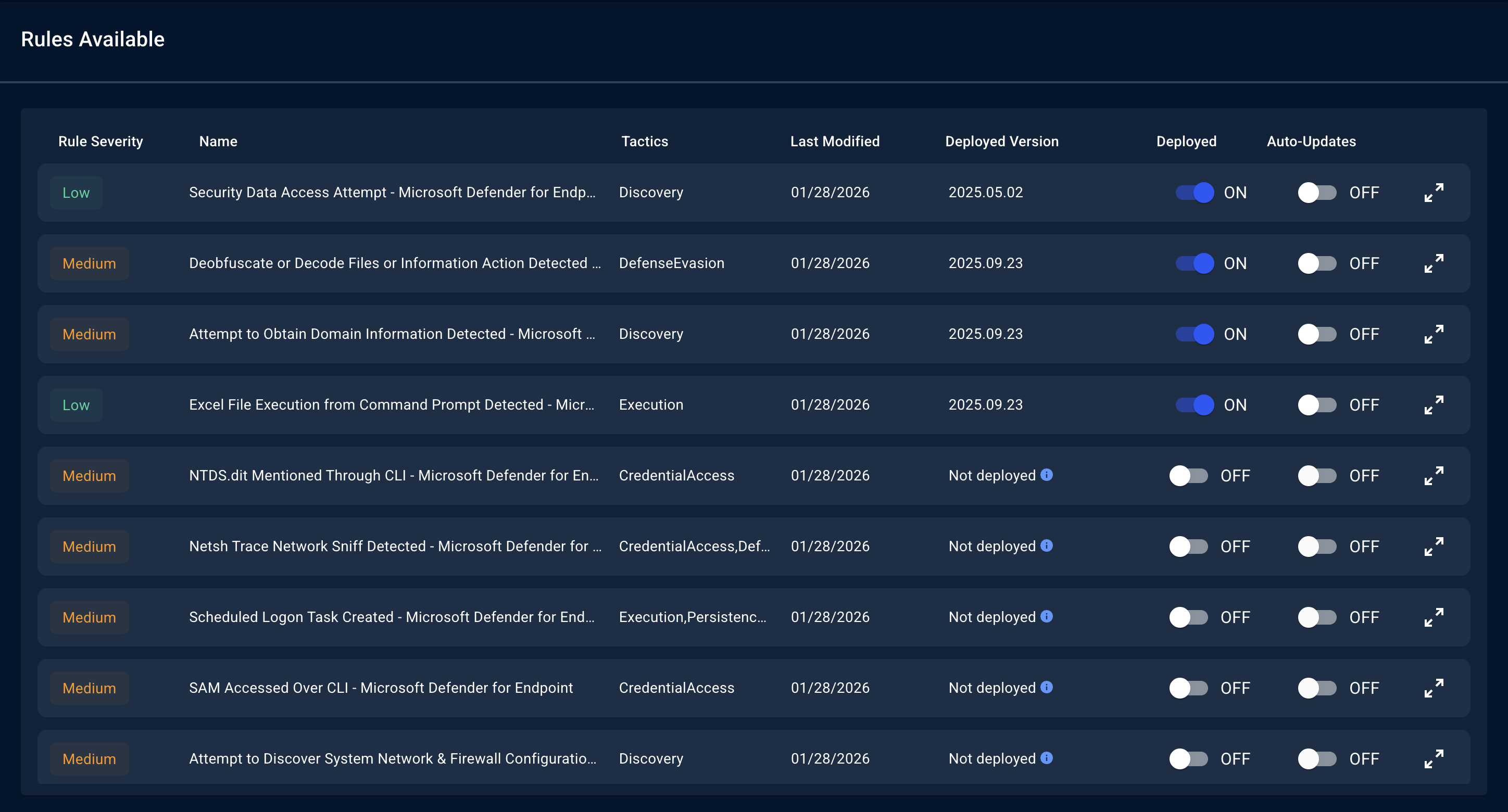
Simple Deployment
Deploying a detection rule is as simple as toggling a switch:Automated Updates
When our security engineering team improves a detection rule—whether to catch new attack variants, reduce false positives, or optimize performance—CMS can automatically update the rule in your environment.Version Management
Every rule is versioned using Calendar Versioning (CalVer). You can see:- Which version is currently deployed
- Whether a newer version is available
- The history of changes to any rule
Key Capabilities
- Multi-Tenant Deployment
- Toggle-Based Activation
- Real-Time Status
- Role-Based Access
For MSSPs and organizations with multiple Sentinel workspaces, CMS enables deployment across all environments from a single interface.
- Deploy to one customer or one hundred—the process is identical
- Consistent detection coverage across your entire customer base
- No need to log into each Azure tenant separately
Analytic Rules Per Data Source Type
CMS provides detection rules for threats across your Microsoft Sentinel data sources, which include some of the following coverage:Identity
- Active Directory
- Entra ID
- Sign-in analytics
Microsoft 365
- Exchange Online
- SharePoint
- Teams
Azure Infrastructure
- Azure Activity
- Security Center
- NSG
Endpoints
- Windows Security Events
- Defender for Endpoint
Network
- DNS Analytics
- Firewall logs via Syslog
- Network flow data
And More
The CMS library continuously expands with new detections mapped to MITRE ATT&CK and D3FEND
Technical Architecture
Direct Integration with Microsoft Sentinel
CMS communicates directly with Microsoft Sentinel through the Azure Resource Manager (ARM) API:| Advantage | Description |
|---|---|
| Reliability | No intermediate systems that could fail or introduce delays |
| Speed | Rule deployments complete in seconds, not minutes |
| Transparency | Every deployment operation is logged with full details |
Background Processing
Rule deployments run as background jobs:- Your browser doesn’t need to stay open during deployment
- Multiple deployments can run simultaneously
- Failed deployments automatically retry
- Notifications alert you when operations complete
Secure Rule Storage
Detection rules are stored in a dedicated Azure Cosmos DB database with:- Encryption at rest
- Version history preservation
- Geographic redundancy
- High availability
Benefits by Role
- Security Analysts
- Security Engineers
- MSSPs
- Security Leaders
For Security Analysts
- Faster onboarding — Start detecting threats immediately with pre-built rules
- Less context switching — Manage detection content alongside incident response in one platform
- Confidence — Know that detection rules are authored by security experts and continuously updated
Getting Started
Prerequisites
Deploying Your First Rule
Configuring Automatic Updates
You can enable auto-update for individual rules or set a workspace-wide default. Rules with auto-update disabled will show an “Update Available” indicator when new versions are released.
Frequently Asked Questions
Will deploying a rule affect my existing Sentinel rules?
Will deploying a rule affect my existing Sentinel rules?
No. CMS-deployed rules are tracked separately and won’t interfere with rules you’ve created manually in Sentinel. They coexist peacefully with your custom detections.
Can I modify a CMS-deployed rule?
Can I modify a CMS-deployed rule?
CMS rules are deployed as-is to ensure consistency and supportability. If you need custom modifications, you can use the rule as a template and create your own version in Sentinel directly.
What happens if a deployment fails?
What happens if a deployment fails?
You’ll see an error message with details about what went wrong. Common causes include permission issues or temporary Azure API unavailability. Failed deployments can be retried with a single click.
How often are new rules added to the library?
How often are new rules added to the library?
Our security engineering team continuously develops new detections based on emerging threats, customer feedback, and industry research. New rules are added regularly.
Can I see what changed in a rule update?
Can I see what changed in a rule update?
Yes. Each rule version includes information about what was modified—whether it’s an improvement to detection logic, a reduction in false positives, or a performance optimization.
What permissions do I need to deploy rules?
What permissions do I need to deploy rules?
You need the Data Source Admin, Content Admin, or Organization Admin role in ContraForce. You also need appropriate permissions in the target Azure tenant for Sentinel API access.
Can I deploy rules to multiple workspaces at once?
Can I deploy rules to multiple workspaces at once?
Yes. CMS supports bulk deployment across multiple Sentinel workspaces. Select the workspaces you want to target and enable the rules—they deploy to all selected workspaces simultaneously.
Best Practices
Start with high-confidence rules
Start with high-confidence rules
Begin by enabling rules with low false positive rates and high detection value. As you gain confidence in the system, expand to broader coverage.
Enable auto-update for standard rules
Enable auto-update for standard rules
For general-purpose detection rules, enable auto-update to stay current with threat landscape changes. Reserve manual approval for rules where you need tight change control.
Review MITRE coverage
Review MITRE coverage
Use the MITRE ATT&CK mappings to ensure you have detection coverage across the kill chain. Identify gaps and enable rules that address them.
Align rules with data sources
Align rules with data sources
Only enable rules for data sources you actually have connected. Enabling rules without the corresponding telemetry will result in rules that never fire.
Monitor rule performance
Monitor rule performance
Periodically review which rules are generating incidents. Rules that never trigger may indicate missing data sources or detections that aren’t relevant to your environment.
Learn More
Product Release Blog
A Better Way to Manage Detection Content
CISA Guidance for SIEM/SOAR
How MSSPs Can Implement CISA Guidance
Multi-Tenant Automation
10 Ways ContraForce Automates Multi-Tenant Management
User Roles Reference
Permissions for Users managing CMS across tenants
Related Guides
Questions about the Content Management System? Contact us at support@contraforce.com.

